I spent decades as a respected financial‐services entrepreneur, building my reputation and credit score from the ground up—only to have them ripped away by the very KYC safeguards I trusted most. One day, my credit‐card issuer called to say someone had rung up dozens of unauthorized charges on my account. I was stunned—but they didn’t even seem embarrassed. Instead, they grilled me for paperwork, then admitted their identity checks had glaring holes that let a fraudster slip in under my good name.
Over the next months, I chased creditors and credit‐reporting agencies through endless phone menus and document uploads. Their “rigorous” KYC processes never once flagged the criminal who opened multiple new lines of credit in my name. Meanwhile, my personal life unraveled, and I was forced into early retirement before turning 65 just to manage the fallout.
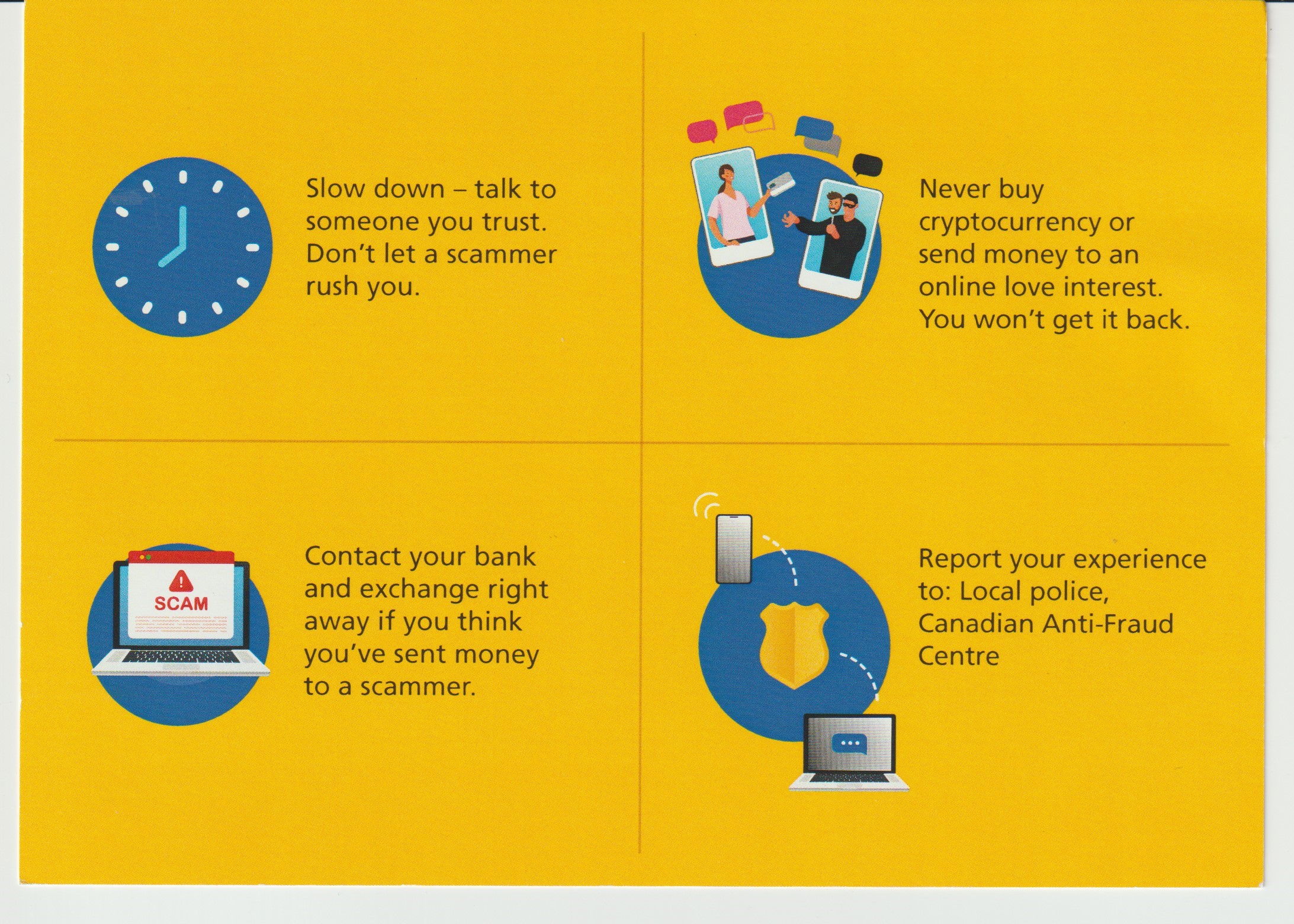
As if that weren’t enough, every few years I must now drag myself down to the local police station, present two government‐issued photo IDs, be fingerprinted, and wait days while they run my prints against six different criminal databases—to prove I’m not the “other” Ted Lee. It’s absurd: I’m treated like a suspect because these institutions can’t be bothered to secure their own onboarding.